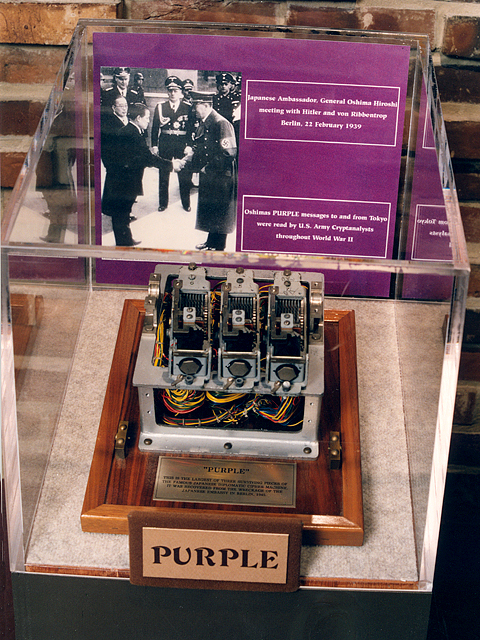
JAPANESE RED, PURPLE CORAL AND JADE CIPHER
GO BACK, USE PURPLE, OR HEAR THE PURPLE MACHINE RUN
INSTRUCTIONS ON USING THE PURPLE MACHINE ON THE MAIN PAGE
Notes and corrections are with the grateful assistance of Geoffrey Sinclair

Not having a written language of their own, in the third century AD, the Japanese began to adopt Chinese ideographs, symbols or pictures which represent an idea or an object, and use them for words of similar meaning in their spoken language. Each ideograph represented one picture, one idea, one meaning and hence it was not difficult to apply the ideographs to Japanese words with the same meaning (Deadly Magic 18). In the ninth century they adopted Chinese pronunciation of compound words made up of several ideographs. This system required all Japanese to learn four or five different pronunciations or readings for each ideograph; there were thousands of ideographs in use.
In order to simplify the written Japanese, Japan also invented two phonetic alphabets each consisting of fifty letters: katakana – block letters and Hiragana – cursive writing (Deadly Magic 19). Katakana was the most abbreviated and simple, was typically used to write foreign words. Hiragana, which is more directly related to Chinese, was to be used for native Japanese words and concepts. All attempts at introducing the Latin alphabet into Japan failed.
It is because of this complex, engrossed language that Japan didn't use Morse code for communication. Instead they keyed messages, developed by the Imperial Navy, according to the syllable of the word in katakana (Prados, 9). As a result, the code contained twice as many dots and dashes. Used prior to and during World War II, it was Japan’s own form of Morse code.
When the U.S. Seized the Philippines in 1898, Japan-US relations were tarnished for the first time. The Imperial Japanese Navy saw the US’ westward movement as "squeezing and poisoning Japan." The relationship worsened at the Washington disarmament conference of 1922 because the US forced Japan a lower warship ratio than they wanted. Americans sought a way to figure out what Japan was planning.
In 1923 the United States Chief of Naval Operations told the Asiatic and Pacific fleet radio operators to listen for Japanese messages. . .perhaps he was unaware that they were transmitted differently than all other. Either way, the operators were able to teach themselves to recognize and intercept Japanese radio communications. One Philippine operator, Harry Kidder, learned katakana syllable through the teachings of the Japanese wife of a shipmate. Kidder was then able to teach himself the telegraphic equivalent of each symbol and thus began to translate the intercepted Japanese messages. At first, intercept operations were only handled on a few ships in the Asiatic fleet.
A few others at the Asian station learned katakana as well, but the translations by all were very haphazard.
In 1918 a Japanese codebook was found and by 1921, it was completely translated by the Office of Navy Intelligence. Only a few copies of the Japanese fleet code were made by the Americans who code named it the "Red Book," and passed it on to the Director of Naval Communications. As a result, the Director then saw the need for a radio intelligence service to be developed. A school was set up in Washington to teach selected radio operators katakana and the Japanese telegraphic codes. When the school opened in 1928, Chief Kidder was the teacher where he graduated three classes. Eight graduates from the school were sent to Guam where they established station BAKER.
Meanwhile, in 1924, a big step was taken to organize transcription when the US bought Japanese typewriters. As a result, the first shore-based intercept station was built in Shanghai that year. The main focus of this station was the diplomatic radio network that served the Japanese consultants throughout China. In the meantime, self-trained operators in the Marine Corp in Beijing also focused on this network. Known as station ABLE, this unit was abandoned after eight years of service in 1935 due to the Japanese threat and lack of personnel. Then the responsibility for the diplomatic network was shifted to the headquarters of the Fourth Marine Regiment in Shanghai. This station, equipped with lots of Navy intercept operators trained in Japanese, was thus renamed ABLE.
In 1930, the men at station BAKER were able to deduce from intercept patterns alone that Japan's entire fleet including reserves had set sail and were engaged in some sort of massive exercise. In fact, these men were right. The Japanese navy had called up its reserves to participate in a practice attack. The US Navy stationed in Tokyo had no idea. Station BAKER sent these intercepts to Washington to be translated. The US government cryptanalysts used the "Red Book" to slowly aid them in the decryption process. Enough was decoded for the Americans to realize that the detected activity was a practice invasion of Manchuria.
The slowness of the decryption of these intercepts led the United States to realize the inadequacy of its facilities for decoding and intercepting messages. Intercept stations needed to be built in Hawaii and in the Far East to aid those in the Pacific Theater. These stations needed to employ an abundance of cryptanalysts, Japanese linguists and intercept operators.
Also in 1930, the Japanese changed their "Red Book." Unfortunately, this new Blue Code was considerably more complex. It was a "four-kana" code unlike the Red Code’s "three-kana" code. The Japanese also complicated this code even more by inserting material from other sections on each page. The result was that the progression of the vocabulary from the old code was broken up making it more difficult to crack. For the next five years, American cryptanalysts worked on deciphering a new codebook, led primarily by the Radio Intelligence Officer of the Asiatic Fleet, Joseph Wenger. There were other available communication sources as well. The Navy attacked Japanese naval codes – for administration, merchant ships, logistics, intelligence – and several cipher machines. Traffic analysis was also available when code breaking failed. Traffic analysis involved an "organizations structure and operation from message routing, message volume, call signs, and operations’ chatter." One of the key tools used is direction-finding; it locates a radio transmitter and through connections can tell where a ship is. Other techniques can be used to plot a ship’s course and speed. Also, by studying the call signs, you can determine which stations are talking. Also increased volume in a certain area can represent increased activity. The hardest part of breaking a code is getting started. One cryptanalyst explained "It first off involved what I call the staring process. You look at all of these messages that you have; you line them up in various ways; you write them one below the other; you write them in various forms and you stare at them. Pretty soon you’d notice a pattern; you’d notice a definite pattern between these messages. This is the first clue." Using all other forms of communication and prediction techniques, he was able to guess and correctly determine Japan's actions. He then used these predictions to translate the signals received during the blackout. He produced a 115-page report that served as a basis for the "Blue Book." The Commander in Chief of the Asiatic Fleet was extremely impressed by Wenger's work and he requested an intercept station in Manila Bay to serve as the "ultimate defense" to protect the surprise attack.
Five graduates from Kidder's classes, meanwhile, had been sent to the Philippines to set up an intercept station in Olangapo. They called themselves station CAST and were moved to Mariveles, then to the Navy Yard in Cavite, and were finally stationed in a bombproof tunnel built for the US Navy at Monkey Point on Correigidor in 1940. In 1942, station ABLE was closed and its personnel and duties were given to station CAST. CAST provided major intelligence support for the Asiatic Fleet. They had interception and cryptanalytic capacity, a direction-finding capacity, as well as extensive liaison with fleet headquarters. Stations CAST’s "claim to fame," however, was that it was the first United States communication unit to track a Japanese warship entirely by monitoring communications. By 1941, station CAST had forty-one radiomen, nine yeomen, and ten crypto-analytical personnel (Prados 83).
In
1936, another station was being built by Thomas Dyer on the windward side of
Oahu, station HYPO, and a new decryption site was created in the basement of the
administration building in Pearl Harbor. Having more staff than station CAST,
station HYPO employed sixty-nine radiomen plus boasted a significant
crypto-analytical facility.
The
Japanese cipher machine which the American cryptanalysts codenamed CORAL is
perhaps the easiest to understand of the three code
machines they employed.
All three machines were built from common telephone stepping switches. These switches had six input wires. Each wire was connected to a wiper, and each wiper could make contact with one of twenty-five terminals. All six wipers moved together, and each one had its own set of 25 terminals to contact.
A solenoid controlled the movement of the wipers. When a current pulse was fed to it, the wipers advanced one position, except that, if the wipers were already at position 25, a spring caused the wipers to go back to the first position. Thus, although the 25 terminals were arranged in a semicircle, the switch acted as though they formed a full circle, with stepping in only one direction.
In CORAL, a stack of five stepping switches did the same job as a rotor would do in a Hebern rotor machine. 26 input wires carried current to 26 outputs, in 25 different ways. The alphabets for each of the 25 wiper positions, unlike the alphabets for the different positions of a rotor, were completely independent and unrelated.
JADE was just about the same as CORAL, except that it was used to encipher messages written with the Japanese katakana syllabary, which has 48 symbols. Thus, it added a shift key to the keyboard. This shift key accompanied a 25-symbol alphabet, which gave equivalents to the 48 kana and the two diacritical marks used with katakana.
PURPLE, the earliest of the three machines, had a somewhat stranger structure. A plug board selected 20 letters of the alphabet to be enciphered through banks of four stepping switches. The other six letters were enciphered by means of only one stepping switch. This division of the alphabet was easily detected through frequency counts, and was perhaps the most serious weakness of the machine. (Another very serious weakness, and also a strong contender for the title of "most serious weakness", was the fact that the stepping switch banks were, for obvious reasons, not removable, so one could never perform the operation equivalent to changing the rotor order.)
The following diagram:
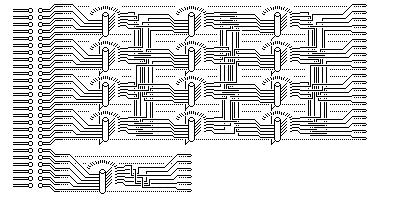
attempts, with many parts omitted, to illustrate how PURPLE worked. The plug board reassigned letters for both input and output. The stepping switches only have fifteen tick marks around them - representing the 25 contacts each wiper actually has. For only one wiper position for each switch or bank of ganged switches, the scrambled arrangement in which the wires are connected to corresponding wires in the next stage are shown. However, the 20 versus 6 division is easily visible in the diagram, as is the general arrangement of the device.
The three banks of stepping switches advanced in the traditional odometer like fashion; when the fast one advanced 25 steps, the medium one would advance one step, and when the medium one advanced 25 steps, the slow one would advance one step. A switch allowed all six possibilities of which bank was fast, medium, or slow to be selected.
The wiring of the plug board was part of the daily secret key of the machine, as was the pattern of stepping switch bank movement. The starting positions of the stepping switches for each message were communicated by an indicator. Both the plug board wirings and the stepping switch start points came from a book which contained all the possibilities that were used, which were limited in number compared to all the possibilities that could be used with the machine.
Purple was an intricate, complicated cipher machine, a complex adaptation of the German's Enigma machine. Cipher machines, which were first used in World War I, can complicate encipherment of plaintext by performing innumerable enciphering operations, easily and with great speed, making enemy decoding extremely difficult. Breaking a complicated cipher produced by a rotor machine is, however, possible. A crib or plaintext for a number of cipher messages, makes this task much easier. Also, the "indicator system" which is the method by which the sender notifies the recipient of the starting rotor positions for each message. By having enough overlapping cribs, it is possible to link the pieces together nullifying the effect of the rotors. This can make the solutions of the coded messages trivial.
Physically,
a PURPLE machine consisted of two electronic typewriters separated by a plug
board and a box containing the cryptographic elements in a series of relays
within an intricate network of wiring (Deadly Magic 63). The plug board had a
plug for each letter of the Roman alphabet. PURPLE simultaneously recorded
plaintext and cipher text. This double machine super-enciphered alphabets, in
other words, repeatedly enciphered the text, with a multitude of manipulated
versions (Deadly Magic 64). Many millions of cipher alphabets of 26 letters were
available for substitution ciphers. The reoccurrence of a word in its original
enciphered text took place about one in 100 signals. Similar to the Enigma
machine, Purple would not encipher any letter to itself. More specifically, an
"a" entered on the keyboard would never be outputted as an
"a." This is why Japan was so fervent in their beliefs that PURPLE was
unbreakable.
The United States was in a bind, they knew that they would need to create a replica of a PURPLE machine, a "shadow" cipher machine, in order to break Japan's newest code. In August 1940, the team lead by William Friedman, senior cryptanalyst, reconstructed a "shadow" of the PURPLE machine. For the following twenty months, US cryptanalysts experimented with wires and switches of the wheels of the "shadow" machine. This was complicated because the positions of the plug board connections were unknown, and the daily starting positions were unknown as well. Several months into experimenting, it was discovered that the starting keys for each day in a ten day period were related. Operators changed the key to form that of the next nine days. The cryptanalysts involved in breaking Purple worked to match "proposed plaintext", a guess as to the text of the original message, that were simultaneously received in Red and Purple to determine proposed plaintext, because they could decode the Red message.
Two major breakthroughs occurred in the PURPLE deciphering dilemma. First, because Japan guarded their PURPLE machines dearly, they did not put one in every diplomatic office; machines were only put into twelve of the Japanese embassies. Therefore, this helped the US cryptanalysts because, since Japan needed to provide some of the same messages to every diplomatic office and embassy, they were forced to use PURPLE and other cipher codes to transmit these messages. Many of these other cipher codes were already broken by the United States. Thus the Americans were provided with the plaintext corresponding to the PURPLE signal. In other words, it provided the Americans with a crib.
Second, Americans staged an electrical failure at the Japanese embassy in Washington and two agents of the American Signal Intelligence Service, posing as electricians, were able to sneak a peek at the actual PURPLE machine. They were able to alter their "shadow" machine according to the information relayed from the agents.
The first fully intelligible message was recovered on September 25, 1940. The break into Purple was especially notable because the machine was even more sophisticated than the German’s Enigma machine, but also, the code was solved entirely by mathematical analysis. Furthermore, the British analysts who solved Enigma could rely on advances made by French and Polish experts…the Americans solved Purple completely on their own.
The
"shadow" machines proved to be so skillful that Americans were able to
receive the decoded message before the Japanese embassy. After a while,
Washington was reading fifty to seventy-five Japanese messages per day.
If the Japanese knew that the United States’ cryptanalysts had cracked Purple, they would change the code immediately. For obvious reasons, the U.S. wanted to avoid this at all costs (Prados 165).
So after PURPLE was broken in 1940, the United States faced another dilemma as to who should know and who should read the decrypted Japanese signals. The following thirteen people were given viewing rights: President Roosevelt, Secretary of State, War and Navy, Chiefs of Staff of Army and Navy and the Intelligence and War Plans Chiefs of the Army and Navy. The obvious dilemma is that if too many people knew that the Americans had broken Purple, word would leak out and Japan would change the code. This would shut the Americans out of all communication interception.
The
next obvious question is, of course, with all this information and the
successful break into Purple, shouldn’t Washington have known about the attack
on Pearl Harbor?
The short answer is no.
These are some notes from others on Purple:
Purple
was a cipher used by Japan during
World War Two to code diplomatic messages to various embassies throughout the
world, not military traffic. The
military deliberately kept the attack information from the diplomats. Even the
final 14 part message to the US spoke of no further point to negotiations, it
was not a declaration of war.
It had also not helped that some in
US Army intelligence, noting the deadlines for negotiations in the Japanese
messages chose to predict war would occur on Sunday 30 November 1941.
Another
reason is the Japanese consulate in Hawaii, unlike the missions in major world
capitals and in Hong Kong, Manila and Singapore, did not receive a Purple
machine, it continued to use the older codes, and these messages were treated at
a lower priority in Washington given they were not in the main Japanese code
system. The biggest clue in all the diplomatic traffic was a cable to
Hawaii on 24 September 1941 wanting regular reports on the warships in Pearl
Harbor and their locations, and the reply (copied to San Francisco) giving the
chosen system on the 29 September 1941. The intelligence appreciation made in
Washington, which was decoding the consulate traffic and cracked these two
messages on 9 and 10 October respectively, was that it was an unusual message
and that it could be a device to cut down on radio traffic, a plan for sabotage,
a plan for a submarine attack or a plan for an air attack.
The decision was taken not to notify Pearl Harbor of the signals.
The Japanese were receiving regular ships in harbor reports from their
diplomats around the Pacific but no others were asked for ship locations. The Japanese message later became known as the “bomb
plot” message, after the attack and is considered the most obvious lost
opportunity to at least put Hawaii on a higher level of alert. However it should be noted in the weeks before the war
reconnaissance from Hawaii concentrated on the approaches from the closest
Japanese bases in the central Pacific. Since
the USN had not learnt of the recent advances where the Imperial
Japanese Navy (I.J.N.) had learned to refuel ships at sea and that it
knew 3 of the I.J.N. fleet carriers lacked the range to sail to Hawaii and
return from Japan, the USN understood approaching from the central Pacific the
only way for the I.J.N. to launch a major strike against Hawaii.
Without enough reconnaissance aircraft to mount a 360 degree search and
needing to preserve the scare aircraft the searches had to be restricted.
"The
breaking of Purple, though unable to prevent Pearl Harbor, later yielded
astonishing insights into Hitler’s plans, gleaned from the messages of the
Japanese ambassador in Berlin; All of this noticeably shortened the
conflict" (FA 151).
Cryptology was a key factor in the US’s victory in WWII. One expert stated that it shortened the was by a year. It didn’t take long for the US and other nations to realize that cryptanalysis is "the cheapest, latest, and truest source of information" (Kahn, 613). Cryptology became one of the world’s most important sources of secret intelligence in World War II. Vice Admiral Walter S. Anderson, the former director of Naval Intelligence summed it up best when he said, "[Cryptology] won the war!" (Kahn 613).
Some sources claim that American cryptanalysts had cracked the Purple code detailing the attack on Pearl Harbor prior to December 7, 1941. It was also suggested that by December 6, Washington had a message that contained the information that Japan and Germany were prepared to declare war on the United States. Washington allegedly remained silent in order to protect the secret of the Purple code. If the Japanese knew that the United States’ cryptanalysts had cracked Purple, they would change the code immediately. For obvious reasons, the U.S. wanted to avoid this at all costs (Prados 165).
But in an interview with Captain Joseph J. Rochefort, USN, he insists that the cryptanalysts at station Hypo (Rochefort's unit at Pearl Harbor), are not to blame for the attack. He says "an intelligence officer has one task, one job, one mission. This is to tell his commander, his superior, today, what the Japanese are going to do tomorrow. This is his job. If he doesn’t do this, then he’s failed." According to Rochefort, he failed at Pearl Harbor.
He offers two reasons for the failure: One, they only had about five months to get themselves reorganized, and two, radio equipment was being withheld and sent to Europe. He explains that on December 7, the cryptanalysts were running information and supplies back and forth from the intercept station which was six or eight miles away. The only way to communicate with the transmitter site, called CXK, was by sending a jeep. This wasted a couple of hours each way. Rochefort also claimed that the wire system was severely inadequate. "It’s like having a million-dollar organization with a ten-cent stamp communications system," explained Rochefort. He claims that on December 1, the Japanese changed a major part of the communication system that kept the Americans from translating and understanding the messages. So although the volume of messages transmitted suggested that something was about to occur, the cryptanalysts couldn’t read them.
An additional source explained that it wasn’t until eight days later that the messages were fully deciphered and translated. But the problem that occurred with Pearl Harbor wasn’t due to intelligence, it was because of policy. Because there were a limited number of resources at this station, the high-level diplomatic cables received priority. The radio intelligence unit was instructed to work diligently on the Imperial Navy’s Admiral Code rather than deciphering diplomatic codes. Furthermore, the bomb-plot messages were deciphered in Pearl Harbor and not in Washington. Since Washington was consistently preoccupied with seemingly more prevalent issues, it is suggested that the messages would not have even been taken seriously by the officials in the capitol (Prados, 166). "The breaking of Purple, though unable to prevent Pearl Harbor, later yielded astonishing insights into Hitler’s plans, gleaned from the messages of the Japanese ambassador in Berlin; All of this noticeably shortened the conflict" (FA 151).
There remains yet another reason why the US wasn’t ready for and didn’t believe that there would be an attack at Pearl Harbor. The traffic analysis reports taken in the four day span surrounding December 7, there was no communication between any of the Japanese carriers. The US concluded that this meat that the carriers were back in home waters. How the Japanese had outwitted the US for in fact "six of the carriers throught to be in home waters were in fact plowing the seas north of Hawaii "(FA 147).
Also in 1942, the United States received many purple messages forecasting an attack at "AF." At the time, the mid-Pacific radio net was intercepting sixty percent of the Imperial Navy’s messages. Furthermore, only about forty percent of the messages were being read. The one main advantage the cryptanalysts had was that they knew the meanings that the Japanese attached to a number of geographical designators, including "AF." Americans presumed that "AF" stood for Midway, but in order to figure out what AF stood for exactly, Nimitz told his operator to send a coded message, in a code that Japan had already broken, that Midway island was out of water. Sure enough, hours later the US received a PURPLE cipher that said "AF is out of water." Indeed "AF" meant Midway. Nimitz then sent his fleet to Midway and how surprised and punished the Japanese were when they arrived. History considers this US victory as one of the most decisive battles of war, as Japan's offensive power at sea was nearly destroyed.
Being aware of Japanese intentions also helped to bring about the death of Admiral Yamamoto, the Commander in Chief of the Japanese navy. Purple intercepted ciphers gave word that Yamamoto was to visit the Solomon islands. The exact details of his travels were also part of the message. The American decided to shoot him down. (Hidden War 130).
After PURPLE was broken in 1941, the United States faces another dilemma as to who should know and who should read the decrypted Japanese signals. The following thirteen people were given viewing rights: President Roosevelt, Secretary of State, War and Navy, Chiefs of Staff of Army and Navy and the Intelligence and War Plans Chiefs of the Army and Navy. The obvious dilemma is that if too many people knew that the Americans had broken Purple, word would leak out and Japan would change the code. This would shut the Americans out of all communication interception.
Hans Thomsen, a German spy, discovered that the Americans were breaking PURPLE. He passed this information onto the Japanese, but they were too ignorant and confident to believe that the Americans could break their code.
After the Battle of Midway, the Americans feared that the success with Purple would be compromised. On Sunday June 7, a front-page story of the Chicago Tribune claimed that the Americans had known the details of Japan’s plan to attack Midway. After much investigation, it was concluded that no one from the Navy Department spoke to any Chicago Tribune reporters…the leak was from somewhere else.
The leak was eventually traced to the Chicago Tribune reporter Stanley Johnston, by way of Commander Morton T. Seligman. Seligman was a former executive officer of the Lexington and shared a cabin with Johnston. Apparently Seligman allowed Johnston to see classified dispatches and one of them was Nimitz’s Midway warning. After taking notes on the message, Johnston left the ship to fly to Chicago.
Inside the Navy, it was argued that the Japanese changed all of their codes after Midway as a consequence of the Chicago Tribune affair. While the Japanese did change some codes and communication practices after Midway, the fleet code was left untouched. It was changed before Midway and would be changed before Midway and would be changed again, but it was out of routine, not as an emergency effort to protect Purple. In other words, the Japanese didn’t know that Purple had been broken. Finally, in 1942, Japan was forced to create a new codebook, as it was obvious that the US had broken Purple.
Purple was a cipher used by Japan during World War Two to code diplomatic messages to various embassies throughout the world. The United States worked solely to untangle and decipher the super-enciphered signals they intercepted from the
Japanese. Once the United States had created a "shadow machine", a Purple machine of their own, they were soon after able to decode the various messages they intercepted. These signals gave them an abundance of important information concerning Japan's plans for war and their scheduled locations of attack, however, the signals didn't carry any information about the attack on Pearl Harbor, at least none that was interpreted in that way. Thus Japan used other codes to transmit messages as well, and the interest in Purple had drawn away all concern for decoding the intercepted messages not transmitted in other ciphers. Because of this, the Japanese attack on Pearl Harbor was inevitable. After the attack, decoding measures on all intercepted codes no matter what the cipher, were heightened and increased. Once war was declared, the United States continued to use the intercepted information to figure out where the Japanese fleet was stationed, headed and set to attack. As a result, the United States surprised Japan at Midway and American victory there proved to be very decisive and boosted American morale. Throughout the war, the United States made various surprise attacks on Japan due to the knowledge they had from Purple ciphers. This ended though, when Japan stopped using Purple in 1943.
Cryptology was a key factor in the US’s victory in WWII. One expert stated that it shortened the was by a year. It didn’t take long for the US and other nations to realize that cryptanalysis is "the cheapest, latest, and truest source of information" (Kahn, 613). Cryptology became one of the world’s most important sources of secret intelligence in World War II. Vice Admiral Walter S. Anderson, the former director of Naval Intelligence summed it up best when he said, "[Cryptology] won the war!" (Kahn 613).
Hans Thomsen, a German spy, discovered that the Americans were breaking PURPLE. He passed this information onto the Japanese, but they were too ignorant and confident to believe that the Americans could break their code.
After the Battle of Midway, the Americans feared that the success with Purple would be compromised. On Sunday June 7, a front-page story of the Chicago Tribune claimed that the Americans had known the details of Japan’s plan to attack Midway. After much investigation, it was concluded that no one from the Navy Department spoke to any Chicago Tribune reporters…the leak was from somewhere else.
The leak was eventually traced to the Chicago Tribune reporter Stanley Johnston, by way of Commander Morton T. Seligman. Seligman was a former executive officer of the Lexington and shared a cabin with Johnston. Apparently Seligman allowed Johnston to see classified dispatches and one of them was Nimitz’s Midway warning. After taking notes on the message, Johnston left the ship to fly to Chicago.
Inside the Navy, it was argued that the Japanese changed all of their codes after Midway as a consequence of the Chicago Tribune affair. While the Japanese did change some codes and communication practices after Midway, the fleet code was left untouched. It was changed before Midway and would be changed before Midway and would be changed again, but it was out of routine, not as an emergency effort to protect Purple. In other words, the Japanese didn’t know that Purple had been broken. Finally, in 1942, Japan was forced to create a new codebook, as it was obvious that the US had broken Purple.
Purple was a cipher used by Japan during World War Two to code diplomatic messages to various embassies throughout the world. The United States worked solely to untangle and decipher the super-enciphered signals they intercepted from the
Japanese. Once the United States had created a "shadow machine", a Purple machine of their own, they were soon after able to decode the various messages they intercepted. These signals gave them an abundance of important information concerning Japan's plans for war and their scheduled locations of attack, however, the signals didn't carry any information about the attack on Pearl Harbor, at least none that was interpreted in that way. Thus Japan used other codes to transmit messages as well, and the interest in Purple had drawn away all concern for decoding the intercepted messages not transmitted in other ciphers. Because of this, the Japanese attack on Pearl Harbor was inevitable. After the attack, decoding measures on all intercepted codes no matter what the cipher, were heightened and increased. Once war was declared, the United States continued to use the intercepted information to figure out where the Japanese fleet was stationed, headed and set to attack. As a result, the United States surprised Japan at Midway and American victory there proved to be very decisive and boosted American morale. Throughout the war, the United States made various surprise attacks on Japan due to the knowledge they had from Purple ciphers. This ended though, when Japan stopped using Purple in 1943.
Cryptology was a key factor in the US’s victory in WWII. One expert stated that it shortened the was by a year. It didn’t take long for the US and other nations to realize that cryptanalysis is "the cheapest, latest, and truest source of information" (Kahn, 613). Cryptology became one of the world’s most important sources of secret intelligence in World War II. Vice Admiral Walter S. Anderson, the former director of Naval Intelligence summed it up best when he said, "[Cryptology] won the war!" (Kahn 613). JN-25 fact sheet, Version 1.1 September 2004. by Geoffrey Sinclair Firstly thank you to Phil Jacobsen for supplying the copies of the documents referenced in this article, his willingness to answer my questions, aid in understanding the documents and suggestions to help accurate presentation of the material. Also to Leroy W. Gardner, Silver Spring, Md. for extracts of the JN-25 code books and help in understanding JN-25. Any remaining errors are the author?s responsibility. This article has two main sections, the first deals with the structure of the Imperial Japanese Navy (IJN) code system now known most widely by the allied designation JN-25. The first section is an explanation of the structure of the code, a diary giving the changes made to the code and the allied resources devoted to cracking it over roughly the first 4 years of its usage. In the second section information is arranged by theme, such as the growth of the United States Navy (USN) section in Washington devoted to cracking enemy codes. It may help easy understanding to look at the tables at the end of the article first before reading the diary section. JN-25 code information is covered until the large scale change over of versions that took place on 5 August 1943. Comment and any corrections welcome, this summary is based on US Navy documents on IJN codes and as such will likely have some errors in them when it comes to the finer points of the codes. Major References Note while these are the locations as written on the documents, the author has been made aware the classification RG38 also appears as Records of the Office of the Chief of Naval Operations, as opposed to Chief Naval Security Group. 1. RG38 CNSG Library, Box 115 5750/197 The activities and accomplishments of GY-1 during 1941, 1942 and 1943. 2. RG38 CNSG Library, Box 115 5750/198 OP-20-GY code breaking progress reports. 3. RG38, CNSG Library Box 116 5750/199 (2 of 3), OP-20-GYP History WWII. (OP-20-GYP was the USN organisation charged with breaking Japanese codes, it was originally called OP-20-GY) 4. RG38, CNSG Library Box 116 5750/202, The History of GYP-1. 5. RG457 HCC Box 578 NR 1391 JN-25 Cryptographic System Archives II, College Park MD. (Note: HCC is Historical Cryptographic Collection) This reference gives the commencement, end dates and designations of the different versions of JN-25 from 1 June 1939 to early 1945 in a spreadsheet. It also gives the number of key and text additives for selected versions from version A-5 onwards. 6. RG457, Records of the National Security Agency/Central Security Service. Entry 9032, Historic Cryptographic Collection, Box 1109. (The JN-25C code books). 7. RG38 CNSG Library Box 119 5750/221, Corregidor Summary of C.I. Activity, undated but around March 1942. The USN divided its code breaking activities against the Japanese into two field units and a headquarters in Washington. The two field units were located in the Philippines and at Pearl Harbor to directly service the Asiatic and Pacific fleets respectively. The unit at Washington was meant to be a research and training unit with responsibility for Japanese diplomatic codes. [ref 3 page 2]. An agreement in November 1940 with the US Army resulted in the Navy being responsible for processing diplomatic traffic on odd numbered days, the Army on even numbered days [ref 3 page 12] Intercepted traffic from the Pacific intercept stations, which in the period just before Pearl Harbor were Corregidor, Guam and Heeia, Oahu, Hawaii was forwarded to the US via the weekly sailing of the Dollar line "President" liners. A small amount of priority traffic could be sent airmail via the Pan Am clippers, which had a small strong box in their hulls. [ref 4 page 5]. This meant the unit in Washington received the messages at best around a week after they were intercepted, and only then if sent by air mail. There was also an intercept station at Seattle, [ref 3 page 1] which also sent its intercepts by mail, it was only after the start of the Pacific war that the mail was sent on a daily basis from Seattle. It was not until June 1942 that a TWX circuit was available to the west coast. [ref 4 page 28]. According to Captain Pelletier, who was working in Washington, "Before the war, we in [OP-20-]GZ were not current with Japanese messages. Our traffic came by slow boat from Cavite [Corregidor]. Guam and Hawaii and by the time the additives were stripped, and the messages logged and printed, we were at least two months behind. I was also informed that my job was to recover code groups and not to worry about intelligence per se." [Albert Pelletier, "Cryptography -- Target Japan" "NCVA History Book" (Turner Publishing Co.: Paducah, KY 1996) p. 30.] Messages from the Pacific intercept stations were only bundled up and mailed weekly. [Frederick D. Parker, "Pearl Harbor Revisited" CCH NSA p33] but ships did not sail every day from those stations. It may be as low as one ship per month called at Guam. Ships that called at Manila made return stops at Guam or Honolulu or other locations. The shortest leg was Honolulu to San Francisco, Los Angeles or Seattle, which is around five days sailing, and as most messages went by rail from San Francisco to Washington, this added seven more days. It seems the pre war delays between interception and arrival in Washington were between two weeks (at the very best) and up to two months depending on the location and ship schedules. Also the intercept station at Seattle, Bainbridge Island, was primarily monitoring the Tokyo-San Francisco commercial link for messages to and from the negotiation team in Washington with probably one position monitoring the Japanese commercial shipping frequencies for ships in the Eastern Pacific Ocean. It was not looking for IJN traffic. The IJN introduced JN-25 as a fleet general purpose system, and within a few months of introduction it was "of first importance in Japanese naval communications" [ref 3 page 4]. Ultimately, on 31 August 1942 JN-25 absorbed the traffic previously carried on the administrative, intelligence and material codes. These code systems had been in use before the introduction of JN-25. [ref 3 page 3]. The intelligence code (introduced in 1935 and called I then JN-82) was cracked and found to largely contain reports on USN traffic volumes, and so work on the system was dropped. The administrative code (introduced on 1 November 1938, called AD then JN-76) was partially readable in 1940, revealing simple things like ship movement reports, a revision of the system on 1 November 1940 made it proof against further cracking. The material code (introduced in 1935 and called MAT then JN-79) was cracked and revealed some information on the IJN building program, like the construction of the Yamato but no details as to size or guns carried. [ref 3 pages 2, 3 and chapter V page 1]. JN-25 was considered "by far the most complex problem to be attacked" [ref 3 page 4] The IJN called the system Code Book D, and the USN originally called the system AN, later the designation was changed as part of an allied attempt to classify the codes used by the Japanese, and it became JN-25 in March 1942 [ref 3 page 11]. Further letters and numbers indicated the different versions of the basic code system being used, thus JN-25A5 is the A version of the code book combined with the 5th version of the book used to disguise the code groups in use, JN-25E23A is the E version of the code book with version 23A of the book used to disguise the code groups in use. JN-25, a code book of 5 digit numbers (also called five numeral groups at times), divisible by three, which are assigned meanings, like phrases, words, letters and numbers. This gives a total of 33,333 valid code group numeric values, in practice some were left blank either as a security feature or to allow for expansion. This part of the system was the code, the substitution of the numeric groups for the plain text. To disguise the numbers a book of 5 digit random numbers, additives, was used, a page of the additive book was a 10x10 table of five numeral groups. This part of the system was the cipher, it was the method of disguising the code groups. At a random point in the additive book the code clerk selected a sequence of additives and added them to the message code groups using false arithmetic (no carrying), these were the numbers then transmitted. In addition another 5 digit code group was added at a known point in the message to tell the receiver which pages the random numbers were taken from, this was called the indicator group or key, it was sent twice in each message to insure against any garbles. The system had a separate list of random numbers used to disguise the indicator group. Ignoring for a moment the indicator group, date/time group, call signs and other information in the message preamble and also ignoring the tables used for super enciphering date/time and so forth, the fundamental JN-25 system for the war was as follows, Message, From Kaga Estimated time of arrival 19th 2130. Code groups, 21936 48222 01905 38832 87039 64527 11520 99708 meaning, one word per group from NGUC Kaga stop ETA 19th 2130 stop. NGUC = next group upper case additive key 02923 41338 00989 15861 28959 90024 23693 18229 code plus additive 23859 89550 01884 43693 05988 54541 34113 07927 encrypted text as transmitted, 23859 89550 01884 43693 05988 54541 34113 07927 [Example from Code Breakers by Hinsely and Stripp] The USN called the book where it wrote down the basic information on the JN-25 code R.I.P, Registered Intelligence Publication. Different versions of JN-25 were given different R.I.P. numbers, JN-25E15 was R.I.P. 74, JN-25G46 was R.I.P.146. The basic information being the complete system of encryption, that is how the code worked, and hints for decryption, and things like date of use of a particular version, but not the recovered code and cipher values, they were kept in a separate list. In this case code means the actual meaning (letter, word etc.) assigned to a given code group. The USN called the random numbers used to disguise the code groups text or cipher additives and the random numbers used to disguise the indicator groups key additives, the British preferred to use the word subtractor instead of additive. Since the basic JN-25 system did not change during the war the methods developed in 1940 and 1941 could be used and refined, there was no need for the allies to start again from square one. What did change during the war was the way the message externals were done, things like where in the message the key indicators were sent to tell the receiver which additives were used and the system under which the indicator group was encrypted. When multiple versions of JN-25 were in use the message preamble had to include a version identifier. From August 1942 onward several channels, that is different code and/or additive books, within JN-25 were set up for separate groups of subscribers which made recoveries more difficult and tedious. The "text preamble" of a message is the radio "heading" with communication data such as call signs, precedence, message number, (external) action addressee, information addressee, originator and group or word count. "Radio call signs, usually Kana-Kana-Numeral or Kana-Kana-Kana in form, were used as action and information addressees and the message originator were originally encoded [not enciphered] from call sign lists (HYOO) that were effective from one to many months until mid-WWII. Then, most radio call signs were normally changed to a Kana-Kana-Kana-Numeral form and the call signs were enciphered daily with a daily changing substitution table." [Phil Jacobsen, private communication.] In summary 1. valid code group numeric values were 5 digit numbers divisible by 3, so 00003 to 99999, giving a possible 33,333 valid code group numeric values. Valid groups could mean anything from a phrase to a letter or number. This was the code. 2. the code groups were disguised using 5 digit random numbers added to them using false arithmetic, these random numbers were called text additives, often simply called additives. This was the cipher. 3. the special group that told which text additives were in use was called the indicator group or key and it was sent twice within the message. The random number used to disguise the indicator group was called the key additive and came from a separate list, not from the text additive book. 4. apart from the code groups containing the message, a header or text preamble was added to the message containing basic information like sender and receiver call signs, transmission date, message serial number and so forth. In some versions of JN-25 there was a message trailer, with information like date/time added to the end of the message. The structure of the JN-25C code book was as follows, information taken from extracts of captured books, [ref 6]. Title Navy Code book D 1, (Encode) Navy Ministry Top Secret #968-1, short title D A, dated July 1941. Copy number 1225 stamped on title page, there was a page for corrections which in this copy has an entry dated 25 April 1942, against the name Admiral Sekiguchi Kozo. The page numbers for the introduction section were in Roman numerals, page numbers for rest of book in Arabic numerals, it appears Arabic numbers were used for all numbers in the actual code itself. The C code book was introduced on 28 May 1942 and used the uppercase or auxiliary table feature introduced with the B code book, where code groups could be assigned two meanings. The table of contents was as follows: Introduction, pages I to XI, Summary of code book organisation page I Code word composition and arrangement page I Summary of text page I Text arrangement order page III Code book usage advice page VII Procedure for translating and writing up code text page XI Part 1, pages 1 to 13 Figures (numbers) page 1 Year, month, day page 7 Examples of symbols page 11 Part 2, pages 15 to 246 Ideomatic text page 15 Main text, including items like verb endings and connectives, page 16 Part 3, pages 247 to 408 Code and common usage text page 247 Staff Agency Units page 249 Imperial vessels page 278 Imperial capital vessels page 290 Foreign vessels page 305 Place names page 329 Kanji code for telegraph use page 365 Romanised spellings page 366 Kana spellings page 369 Supplementary specialised texts page 397. The final pages, after part 3, were columns of unallocated code groups with blank meanings, available for expansion purposes. Note parts 1 and 2 were printed in black ink and part 3 was printed in blue ink. Part 3 had the uppercase or auxiliary table meanings, repeating some of the code group values used in parts 1 and 2. The different colour ink was used to clearly distinguish part 3 of the book. It appears the code groups in part 1 were chosen from the range of values 73143 to 99999 such that no two groups in the section had 3 identical digits. A page consisted of 4 pairs of columns, each pair being code group value (the 5 digit number) and its meaning, each column being separated by a vertical line. There were 45 lines with every third line underlined to break up the page horizontally. So there were 180 groups and their meanings per page if the page was full. Code group meanings included the numbers 1 to 1000, and each day?s date in month day format, plus groups for early, mid and end of each month, so for example 82216 was "early February". For part 2 the initial page, number 15, was the same layout as in part 1. However on this page there were blank entries throughout the page, both the code group value and meaning left blank, to allow for future expansion. For the rest of part 2 of the code book the pages were 3 pairs of columns, each column separated by a vertical line, each column consisting of 45 lines with every third line underlined to break up the page horizontally, plus, at the bottom of the page, a single line consisting of 4 pairs of code groups and their meanings, so a maximum of 139 pairs of code group and meaning per page. While there were normally 139 code group values printed on each page some had not been given a meaning, clearly reserving them for future use. The need to leave the gaps was driven by the way the section had been organised in alphabetical order, so page 25 started with words that begin [Bin], page 162 with words that begin [Sei]. The meanings for each code group value were given in Kanji, but the page headings were in Romanised script, so page 162 had the heading [Sei-Seki] for example. Part 2 of the code book used code group values from 00003 to 99999, less those used in part 1 or reserved for expansion in the section given at the end of the book, after part 3. The code groups in the final line on the page were case. For example on page 24, code group 80769 means wa (which follows the subject of a verb), code group 01878 means ni (preposition meaning "in, at, on"), code group 48705 means no (the possessive) and code group 68436 means wo (object of a verb). The code groups on any given page were to be used for that page only. Part 3, the uppercase or auxiliary table meanings, written in blue ink, as opposed to the black ink of parts 1 and 2, this part used code group values 00003 to 67959. The first two pages (pages 247 and 248) and most or all of the pages from page 365 on (Kanji code for telegraph use on) had 4 pairs of columns, columns separated by vertical lines, 45 lines per column, plus a single line at the bottom of the page consisting of 3 pairs of code groups and their meanings, so 183 pairs of code group and meaning per page. Like in part 2 pages usually had the code group values printed for each line in the code group value column, but with some had their meaning left blank. As a minor aside some of the punctuation was given along with the name in English, so, for example, code group 52752 has the meaning, ": ((Colon))". The page layout of most of the rest of part 3 was 3 pairs of columns, each pair being code group and meaning, columns separated by vertical lines, each column with 45 lines, again each third line underlined. There was a single line at the bottom of the page consisting of three pairs of code groups and their meanings. So 138 pairs of code group and meanings per page, code groups in the line at the bottom of the page had the meanings signalling uppercase code groups were next. For example, at the bottom of page 365: 73476 -- Next 1 code group is part 3 code group, 86259 - Next 2 code groups are part 3 code groups. 92142 - Next 3 code groups are part 3 code groups. Another example, on Page 327: 98823 -- Next 3 code groups are part 3 code groups. 78924 -- The following is [are] part 3 code group(s). 81675 -- Close [end] part 3 code group(s). Page headings were in Kanji script for most of the section, reverting to Roman script it seems for pages 278 to 367, the Imperial Capital Ships to Romanised spellings sections. The foreign ships lists were broken down by country and then listed alphabetically, often with their Romanised spellings as well as Kanji characters. Place names were listed alphabetically and again often with the Romanised spellings as well as Kanji characters. The Romanised spelling section beginning on page 366 contained groups for the basic alphabet, common combinations of letters, like rr, ville, a few words like the and ton and the compass directions, like SSE. Part 3 does come across as a self contained easy to use sub code, having code groups for numbers and dates like part 1, plus many common terms, like "Navy Minister", rather than the basic grammar of part 2. Also "Part 3 terms are very succinct, in that they may be used in operational brevity messages -- messages that are sent very quickly, when the ship is under duress, for example. Some examples: 1) foreign ship sightings, 2) foreign or domestic ship sinkings, 3) notification of battle -- impending or in progress, 4) sea position locations -- '126 degrees and 30 minutes'" [private communication to the author, from Leroy W. Gardner] The structure of the JN-25C decode book was as follows, information taken from extracts of captured books, [ref 6] title Navy Code book D 1 (Decode), Navy Ministry Top Secret #968-1, short title D A, dated July 1941. Copy number 1225 stamped on title page, making it the pair of the encode book described above. The book was in 2 parts, pages 1 to 250 were part 1 and contained the code groups from parts 1 and 2 of the encode book, code group values 00003 to 99999, but listed in code group numerical value order and printed in black ink. Part 2 of the decode book was the code groups from part 3 of the encode book, the auxiliary table or uppercase part of the encode book, code group values 00003 to 67959, listed in code group numerical order and printed in blue ink. A page consisted of 3 pairs of columns, each of 45 lines with every third line underlined and columns separated by vertical lines, similar layout to the encode book. A difference was the code group value columns only contained the last 3 digits of the code group number, the column heading was the first two digits of the first code group number, and the first two digits of the final code group number was repeated as line 46. The exceptions to the 3 digits rule were line 1, line 45 and if the value of one or both of the first two digits changed, then the whole 5 digits of the code group number was printed. So for example the middle column of page 298 was headed 18, the first code group value printed was 18936, the second was 939, in the middle of the column comes the sequence 996, 18999, 19002, 005, the last value in the column was 19068, and line 46 had the value 19. As a further aid to quick location, on the side of each page, outside the left column for even page numbers and the right column for odd page numbers, the first digit of the code groups on the page was printed in reverse ink, so a white number on either black or blue background. An idea of the structure of an additive book can be determined from the captured copy of additive book 10, which in fact was not used. The cover page says Navy Code Book D, general purpose additive table #10, short title D 1 R 10. The title page says Navy Ministry Secret #924, Navy Code Book D, general purpose additive table #10, date 5 July 1941. The page is stamped 4th Fleet HQ. There were 2 pages telling how to use the book. Next came 12 pages of key additives, to disguise the groups signalling which text additives had been used, the keys. Remembering that in the C version of JN-25 the key additive was selected according to the message serial number. Each key additive page consisted of 4 pairs of columns, each with 10 lines, all lines underlined and columns separated by vertical lines. The left column of each pair had the message number, starting at 1 on the top left of page 1 and ending with the number 480 on the bottom right of page 12. So the message numbers of left column on page 1 were 1, 2, 3 and so on to 10, the second column of message numbers was 11 to 20 and so on through the section. Beside each message number was a 10 digit number using all 10 digits from 0 to 9 and this was the value used to disguise the message key or indicator groups. The column headers were in Kanji but the start and ending message numbers for each page were printed in Arabic numerals as a page header, so page 1 had 1-40 on the top right of page, page 12 had 441-480 on the top left of page. After the key additives section there were 500 pages of text additives, each page in this section had 10 columns each of 10 lines, so all up 100 text additives per page. The lines were marked 0 to 9, top to bottom and the columns were marked 0 to 9 left to right. The page header was the page number. As can be seen from the dates the code materials were prepared many months in advance, the C code book was scheduled to go into service around 1 May 1942 and the number 10 additive book perhaps 2 or 3 months later, the above books were date stamped July 1941. JN-25 timeline, with usage dates and code designations from reference 5, 1 June 1939 the A version or JN-25A introduced along with additive book 1, A-1, the number 1 additive book stayed in use until September 1939, the A code book until 1 December 1940. The IJN designation was D IPPAN RA1, using code book D. At the time the new system was called AN by the USN. It is understood only one code group book was issued, with the code groups assigned in "alphabetic" order, the code therefore being described as unhatted, but this single book made it very time consuming to decrypt a message. It should be noted the assignment order was in fact primarily by the Japanese syllables, which were then sorted into English alphabetical order, rather than strict kana order. There were 30,000 text additives, a book of 300 pages each with a 10 by 10 grid of 5 digit random numbers, clerks were to always start using the additives from column 1. There were 999 key additives, to be chosen by date, these were used to disguise the indicator group, the group that told the receiver which additives had been used. Code clerks were meant to start encoding somewhere in the middle of the message in order to avoid the weakness of stereotyped message beginnings, a begin message here group was inserted into the transmission to show where the message really began. The code groups themselves were 5 digit numbers divisible by 3, so a possible 33,333 valid groups, of which around 30,000 were being used, the rest reserved for expansion. [ref 3, pages 4-6] [ref 4 pages 2-4] Special code groups could be used to replace repeated words. Names like Manila could be rendered as a single word or as 3 Kana particles or as an area designator or as Kanji characters or as six separate letters, since the code had an English alphabet. [ref 4 page 2] Each unit was assigned a start point in the text additive book and was meant to start working through the book from that point, not repeating the use of the same additives until they had returned to the starting point. [ref 3, pages 4-6] The indicator group was constructed as follows. The page number from where the first additives had been selected was multiplied by three, then one was subtracted, the result then multiplied by 100, the line number of the first additive used on that page was multiplied by 10 and added to the page number calculation and a random number was used as the 5th number, in the units column. So page 213, line 5, random number 7 would come out as 63857. The five digit key additive, selected from the list according to the current date, was used to disguise the indicator group, this disguised group was added both the start and end of the message text, being repeated to guard against transmission errors. [ref 4 page 3] A serial number (The SMS or Secret Message Serial) was then added before the first indicator group and a plain text date/time group was added to the end of the message, after the second indicator group. Finally a header of to/from call signs, the number of message groups in the message and "other information of use to radio operators" was added to the beginning of the message and enciphered using a substitution code, this being called the text preamble. The message was then ready to be sent. [ref 3, pages 4-6] From the start it is clear many clerks ignored the "start in the middle of the message" and "work through the additive book" orders. When added to the stereotyped openings and reports this became a way into the code. As a further aid once the system was understood by the allies the conscientious clerks, the ones who are following the text additive instructions, were tracked as they gave insight into the whole additive book and keying system, already compromised by the heavy use starting on page 1 line 1, or else page x (where x is a low number) line 1. It appears 10,000 of the text additives were enough to read 60% of the messages even when the additive book had 50,000 entries. [ref 3 chapter V pages 8-9] 1 September 1939 the change over to additive book 2, JN-25A2, or D IPPAN RA2, additive book 1 had been in use since 1 June. 1 December 1939 the change over to additive book 3, JN-25A3 or D IPPAN RA3 1 June 1940 the change over to additive book 4, JN-25A4 or D IPPAN RA4, in use until 1 October 1940. "Early (Northern) Fall" 1940 the US code breakers realised the system for numbers in JN-25A was the same as the old "S" code the US has the code book for, the code group was the number itself multiplied by a constant. In a single day of checking the high frequency code groups the code groups for the numbers 0 to 999 fell out, 1/30 of the total code. Since all code these group values were divisible by three it confirmed the tentative code group values previously assigned were correct and told the code breakers valid code group numeric values were divisible by three. [ref 3, page 9 and ref 4 pages 11-13] After this discovery the task of further recoveries and exploiting traffic was largely shifted to Corregidor in the Philippines, which for a time in 1940/41 was the largest USN code breaking unit, having completely absorbed the Shanghai unit in December 1940. [ref 3, page 10] (The document SRH-179 notes that the personnel from Shanghai were transferred to Corregidor in phases from August to December 1940. The last group of ten men from Shanghai reported to Corregidor on 16 December 1940. Just before this date the intercept and decryption efforts at Shanghai were shut down.) The largest claim appears to be an error in reference 3, since Washington had more cryptanalysts, it appears the reference is counting all staff, including positions like intercept operators at Corregidor. In effect Washington declared JN-25A "completely solved" and "completely broken", that is the system was understood and the remaining work was in recovering additive groups and assigning meanings to code groups, then exploiting the results. The result was most work in Washington was directed at the earlier, now superceded versions, to try and recover the underlying code groups, since there were many more messages in those versions, the keys of the latest text additive book were also targeted as intercepts built up. No attempt was made to read current traffic. [ref 4 page 14] In fact the size of the system with 33,333 code groups and 30,000 to 50,000 additives meant it was too large for a small number of workers "to read it on a current basis" [ref 3 page 10], work was therefore directed to recovering the code and exploring means of rapid attack on the additive groups. 1 October 1940 introduction of additive book 5, JN-25A5 or D IPPAN RA5, in use until 1 February 1941, additive book 4 had been in use since 1 June 1940. The text additive book is changed to 500 pages each of 100 numbers, so a total of 50,000 numbers and now clerks can start selecting numbers from any column on the page rather than being mandated to start in column 1. The indicator group (key) system is changed, it is now the third and fourth groups transmitted, disguised by a 10 digit random number. The Japanese chose the subset of 10 digit numbers using all 10 digits, rather than allow digits to be repeated, so 1,234,567,890 is a valid key additive but 1,234,567,899 is not. To create the indicator group the system is changed as follows. The page number the first additive has been selected from is multiplied by 2, then 1 is subtracted and the result multiplied by 100, the line number the first additive is multiplied by 10 and the result, along with the column number of the first additive are added to the result of the page number calculation, so page 123, line 6, column 9 gives a value of 24569. The first and second groups of each message are the Secret Message Serial number and operate as a key additive selector, rather than the key additive being selected by date as had been done previously. [ref 4 pages 16-17] Some 1,300 A code groups meanings had been recovered by the end of November. [ref 2, December 1 1940 report]. In November 1940 it was Hoped that the code breakers could move to reading current JN-25A traffic by the end of the year. "This hope, which was held throughout November, 1940, vanished, ironically enough, on December first ?." [ref 4 page 17], the IJN had changed the version of JN-25 code book in use. It should be noted when counting the number of code recoveries that the literature has many examples of the problem of erroneous recoveries of both code group meanings and values as well as text additive values. That is values that were subsequently found to be wrong, meaning new ones had to be substituted in their place. When the British and Americans combined their effort in 1941 for example, the British were critical of many of the USN recoveries as being erroneous. Corrections to previous bad values was an on-going effort. So it is not simply a case of assuming a steady increase in the number of recoveries and that each recovery was completely correct. See for example the number of changes made when in 1945 the USN did more work on the B7 and B8 versions of JN-25 (see below). See also the entry for 10 March 1942, where the recoveries are listed by how confident the allies were about the assigned meaning. On 1 December 1940 the B version (or JN-25B), a new code book but using same indicators and additives, JN-25B5 or D IPPAN RA5 was introduced, replacing the A version which had been in use since 1 June 1939. The B code book remained in use until 27 May 1942. This version was called AN-1 by the USN at the time, it was still known as code book D by the IJN. It introduced upper case or Auxiliary table (two meanings per code word), hatted (code groups no longer in alphabetical order so 2 books, one in code group number, the other alphabetical order), and 3 extra tables for 1) position, 2) geographic designations and 3) date time groups. The third "table" for date time groups was not like the geographical designations but a separate 12 x 31 substitution cipher table rather than a one for one code group substitution. Like the earlier instructions to start in the middle of messages it appears the date/time table was not always used instead the date was sent using the code groups for the relevant numbers or dates. This is confirmed by the fact the C code book still had code groups for dates and times, it appears the date time table was reserved for important dates. In a change from the A version, where the code groups for the numbers were related to the number the B version had a garble table for number and date groups. The table provided a sum check for the first 3 digits and also for the last 2 digits of the code group, and this garble check idea remained in use throughout the war. It proved to be a major weakness once it was recognised, and recovery of the table was regularly used as the first step in breaking new versions of JN-25 throughout the war. [ref 4 page 25] The reference does not give the date when the allies first realised the presence of the table in the B version, the text implies October or November 1941. Note this is not the same as the 12 x 31 date/time table mentioned above, rather it was meant as a garble check for the routine date and number groups, while the 12 x 31 date/time table replaced the date groups and was apparently only used when extra security was required. The first 2/3 of the code groups in the book were given 2 meanings, so some 55,000 meanings were in use. Common words had multiple code groups assigned to them. According to an article in the US Naval Institute Proceedings in June 1979 by/during 1941 the additive book had 50,000 numbers. The article is a translation by Edwin Layton of a section of chapter 13, volume 45 of the Japanese Defence Agency War History series. The article notes the geographic designators and date time tables remained the same for the rest of the war. By working on the A-5 and B-5 messages, the former for text additives to apply to B-5 messages, the latter for code group values, code group values could be recovered. While additive book 5 remained in use the USN exploited blunder by placing the entire Corregidor effort and most of the Washington effort on the current cipher and code recoveries [Parker, "Pearl Harbor Revisited" p. 20]. In Washington this meant 2 or 3 cryptanalysts worked on additive recovery during "the winter of 1940" [ref 3 page 10]. It appears after this period the Washington unit reduced its level of effort against JN-25 until mid 1941. 1 February 1941 the change over to additive book 6, JN-25B6 or D IPPAN RA6, this book remains in use until 1 August 1941. For this additive book the Japanese simply rearranged the key additives, rather than changing them, making the key recovery simple. [ref 4 page 19]. The replaced additive book, number 5, had been in use since 1 October 1940. Initially Corregidor is put on B-6, Washington continues work on A-5 and B-5 messages. [ref 4 page 19] The GY-1 code breaking section in Washington is 10 people, all military personnel, in the first quarter of 1941. [ref 1 page 4] It should be noted this unit was also tasked with the ever increasing work in decrypting Japanese diplomatic messages beginning in the northern Spring of 1941. The unit in Hawaii has been set the task of penetrating the code designated as AD by the USN, also referred to as the Admiral?s code, or Administrative code. Hawaii will continue this work until just after the Pacific war begins without being able to read the code. By the end of February 1941 some 1,600 A code group meanings had been recovered, but no B code group meanings. [ref 2 February 1941 report, dated 1 March 1941] In the first 3 months of 1941 there were 10 USN personnel working on JN-25, this was raised to 16 in June [ref 4 page 21] In early 1941 the US and the UK code breakers (mainly at Singapore, the Far East Combined Bureau [FECB]) joined forces, both countries have around the same amount of code and additive recoveries, with many overlaps but the bulk of the recoveries are new to the other country. [ref 4 pages 21-22]. The first exchange of raw traffic by cable to London was in May 1941, though these did not include JN-25 messages. An experimental teletype line is laid to Winter Harbor, Maine to enable sending intercepts to Washington electronically, the line is brought into use in March 1941. [ref 4 page 22] Also during the [Northern] Spring of 1941 the use of IBM machines to help in finding additive values was perfected, the work was initially slow due to a lack of equipment. Later the USN had purpose designed machines built. [ref 4 page 22] The improvement in capabilities, from the additional manpower and better techniques can probably best be summarised by the fact a review in April 1945 found the allies had around 36,000 text additives from the B-7 version, used in late 1941, versus around 5,000 that had been recovered from the A-5/B-5 versions, which were in use in late 1940 and early 1941. In 1941 Washington was receiving on average 7,000 JN-25 original messages plus 11,000 duplicates per month. This average level continued until mid 1942, [ref 1, page 7] These made up approximately 60 to 75% of the IJN messages (depending on the month) received in Washington [ref 1, page 1] "Early [Northern] Spring 1941" the auxiliary table or uppercase feature discovered, along with the table indicators [ref 4 page 19]. Allied code group meaning recovery status, for JN-25B, April 1, 1941: "approximately 300 values recovered" (also there were 1,800 A code groups recovered showing the continued work on that system, up from 1,400 at the end of February) Selected personnel were receiving 1 hour per day Japanese language training. May 1, 1941: "approximately 400 values recovered" June 1, 1941: "approximately 1100 values recovered" In June 1941 the Washington unit organised a formal group to work full time on additive recovery. [ref 3 page 10] July 1, 1941: "approximately 1100 values recovered" August 1, 1941: "approximately 2000 values recovered" [ref 2, April, May, June, July and August 1941 reports] 1 August 1941 change over to additive book 7, JN-25B7 or D IPPAN RA7, this book remained in service until 4 December. Additive book 6 had been in use since 1 February. In September 1941 it was noted the code groups used to indicate following upper case or auxiliary table values invariably began with a thrice repeated digit, since these indicators appeared frequently in messages it gave a quicker way to remove the text additives. The method was called the difference table, discovered independently by Washington and Corregidor [ref 4 pages 24-25] Allied code group meaning recoveries, Sept 1, 1941: "approximately 2000 values recovered" Oct 1, 1941: "approximately 2400 values recovered" "Completed during October 1941" Nov 1, 1941: "600 values recovered" [i.e., a total of 3,000 values as of this date] "Completed during November 1941" Dec 1, 1941: "800 values recovered" (i.e., a total of 3,800 values as of this date) [ref 2, September, October, November and December 1941 reports] 4 December 1941 additive book 8 introduced, JN-25B8 or D IPPAN RA8. This book will remain in use until 27 May 1942, the longest since the number 3 additive book which had been in service for 6 months from December 1939 on. The replaced additive book, number 7, had been introduced on 1 August. To create the indicator group the system is changed as follows. The page number the first additive has been selected from is multiplied by 100, the line number the first additive is multiplied by 10 and the result, along with the column number of the first additive are added to the result of the page number calculation, so page 123, line 6, column 9 gives a value of 12369. In addition, for the first time the ending point of the chosen additives is sent, as the second last group of the message. [ref 4 pages 27-28]. 7/8 December 1941, Pacific war begins. On 9 December Hawaii started on JN-25 but it looks like the station did not have the materials to really start working on JN-25B until about 11 December 1941 or a few days later. Another date given is 10 December. The materials had been sent out by Washington around September 1941, they were misrouted and were finally found in a Registered Publications depot. The disruption of the Pacific mail system meant Washington had to mark time for a month before B8 traffic was available to it in quantity though it did do some key recovery work. [ref 4 page 27]. In December 1941 or early 1942 use of the secure "Copek" radio channel was allowed to link the code breaking groups. [ref 4 page 29]. The channel had been set up some time previously for top secret information, now the code breakers were allowed to use it for exchanging information. Allied code group meaning recoveries, "Unfinished or continuous" Jan 1, 1942: "Approximately 6,180 values recovered". [ref 2, January 1942 report] In the final quarter of 1941 GY-1 is 22 personnel, 9 officers, 10 enlisted men and 3 civilian men, this is an increase of 1 man per month on average since the start of 1941. [ref 1, page 4] All up in December 1941 USN Communications Intelligence personnel were distributed roughly 1/3 in the Asia/Pacific region and 2/3 in the Atlantic region (including Washington). The Atlantic, Navy department area held 53 officers and 157 cryptoclerks, 178 personnel at the interception stations and direction finding control plus another 60 in outlying direction finding stations, total 448 personnel. The Pacific area held 12 officers and 18 cryptoclerks, 72 personnel at the interception stations and direction finding control plus another 84 in outlying direction finding stations, total 186 personnel. The Asian area, Corregidor, held 9 officers and 19 cryptoclerks, 42 personnel at the interception stations and direction finding control plus another 8 in outlying direction finding stations, total 78 personnel. There were a further 6 officers and 25 clerks classified as "in transit" as of the report date. All up some 738 personnel. [Parker, Pearl Harbor Revisited page 30] Total messages read by the USN per month in Washington during 1941, none. [ref 1, page 8]. The code breakers in the Philippines are said to have managed to break out some simple messages, "invariably ship movement reports: arrivals and departures, together with some fragmentary schedules. The cryptanalysis of the ciphers had outstripped the facilities for code recovery." [ref 4 pages 25-26]. Contradicting this claim is the fact none of these claimed decrypted JN-25B messages was of such intelligence value as to be included in Corregidor?s daily Comint Summary. Also only one so-called "movement report" was included in the Corregidor Comint Summary, on 30 November 1941 and this report could have been from one of two other methods of sending this information by radio besides JN-25B. The personnel from Corregidor, such as Commander Rudolph Fabian and Captain Duane Whitlock , indicate nothing of any intelligence value was ever obtained from JN-25B decrypts before the war broke out. It should be noted reference 4 is a document written in Washington, with problems in obtaining input from the people who were on Corregidor in 1941 and therefore appears in error on this point. (For Fabian's testimony see Hewitt Inquiry, Pearl Harbor Investigating Committee 36/31) Also "JN-25 played no part in the Radio Intelligence story of Pearl Harbor." [ref 3 page 11] and "JN-25, therefore, has no part in the story of Pearl Harbor. What "might have been" there is a story confined entirely to the Japanese diplomatic, not to the Naval communication channels." [ref 4 page 26] "It should be emphasised that recoveries on Japanese Naval [code] systems before Pearl Harbor yielded cryptanalytic information rather than intelligence. The limited number of skilled cryptanalysts and language specialists made it impractical to produce current intelligence except in the diplomatic field" [ref 3 page 3] In the first quarter of 1942 GY-1 is 41 personnel, 9 officers, 30 enlisted men, 1 civilian man and 1 civilian woman. [ref 1, page 4] This is nearly double the staff numbers of three months previously. On 14 February 1942 the Navy department Radio Intelligence section in Washington is reorganised, with 16 sub sections, section GYP is given the job of current cryptanalysis, section 20-G the task of traffic analysis, receiving, routing and IBM machine processes. [ref 4 page 28] On 17 February Hawaii is ordered to forward all radio intelligence reports and intercepted messages by air mail to Washington, so the Washington unit can assist the code breaking effort more effectively. [ref 4 page 29]. Washington used radio messages to send additive recoveries to Hawaii [ref 4 page 51]. On 27 February 1942 battle of the Java Sea. March 1942 the designation JN-25 is adopted. Around late March Corregidor reports as of 10 March 1942 it had completed a punch and reprint of the AN-1 (JN-25B) encode and decode books. These comprised 3522 confirmed, 70 good, 2185 questionable, 3531 very questionable and 939 no classification code group recoveries, total 10, 247 groups. [ref 7] "The new reprint of both encode and decode sections contains all values recovered and received up to March 10, 1942." On 18 March 1942 the Washington code breaking group was ordered to begin decrypting current JN-25 traffic. Two weeks of experiments followed to determine the most efficient method for rapid decryption. The solution was a production line, one person would log the message, another would apply the keys, another removed the text additives, the last person would write down the code group meanings in Japanese. The message was then sent for translation. [ref 4 page 29, 30] On 5 April 1942 start of IJN Indian Ocean raid. On 18 April the last of the code breakers was evacuated from the Philippines. [ref 4 page 29] They mainly went to the joint US Australian unit in Melbourne. 4 May 1942 the battle of the Coral Sea begins. In May 1942 the date/time table was solved at Hawaii, Lieutenant Joseph Finnegan being credited according to Edwin Layton [And I was There, page 427-428] 28 May 1942 Introduction of the C code book plus new additive book 9, JN-25C9 or D IPPAN RA9, (The Japanese called it code system D-1, from Proceedings article). This version stays in use until 14 August 1942 and is then replaced by the D version of the code book. The C-9 version replaces additive book 8 which had been in use since 4 December 1941, and the B code book which had been introduced on 1 December 1940. It is the first time since the introduction of the system the code and additive books have been changed at the same time. In the second quarter of 1942 GY-1 is 98 personnel, 12 officers, 70 enlisted men, 1 civilian man and 15 civilian woman. [ref 1, page 4]. This is over double the personnel from the previous quarter and over 4 times the level of the last three months of 1941. In the period December 1941 to June 1942 Hawaii recovered some 25,000 text additives, in the March to May period Washington supplied over 16,000 more. [ref 4 page 51] June 1942, a TWX circuit is set up from Washington to the US west coast, enabling electronic forwarding of messages as opposed to the daily mail delivery from Seattle. [ref 4 page 28] 4 June 1942 the battle of Midway begins. 7 August 1942 the US invades Guadalcanal. Early August Marines on Guadalcanal capture a JN25C code book. 15 August 1942 introduction of D version code book plus additive book 10 Jo, JN-25D10 Jo or RO 1 RA 1, and stays in use to 19 October 1942. It replaces the combination of the C code book and additive book 9, the C-9 version had been introduced on 27 May 1941. The number of text additives is changed from 50,000 to 100,000, key additives from 999 to 1,000. This version was meant as a general purpose system for all naval forces on land and sea excluding picket boats, gunboats, hospital ships, rescue ships and labour battalions. (For the information on which code book was for what purpose see [ref 3 chapter V page 3]). 15 August 1942 JN-25D16A Jo version, RO 2 RA 1. This is the first case of multiple versions of the code running at the same time, from now on there will be more than one combination of code and additive book in use at the same time. This version uses the D code book with additive book 16A Jo and stays in use until 15 October 1942. 15 August 1942 JN-25D16B Jo version, RO 3 RA 2, running to 15 October 1942. The D-16-A and B versions were general purpose systems for the high command. The traffic in the high command systems was so limited the D-16 versions were never broken and this state of affairs continued for the rest of the war for the high command "channel". (For the information on which code book was for what purpose see [ref 3 chapter V page 3]) A series of 3 digit numbers from a 9 x 9 garble table assigned in 10 day blocks was used to distinguish which version a message was being sent in. [ref 3 chapter V page 4] Until the allies figured out this table showing there were multiple versions of the additive books in use there was some confusion, offset by the fact there was very little D-16A or B traffic intercepted to really confuse things. [ref 3 chapter V page 4]. The D version also altered the method of enciphering the indicator or key group. A 15 digit number is used to disguise the starting point of the additives used, the start position was sent twice and the end point of the selected additives was also sent, as a third 5 digit group. The version indicator group, sent as the third enciphered group in the message, was used to choose the 15 digit number from a list of 1,000 such numbers, up from 999 in all previous versions. This meant for the first time the IJN changed the code book, additive book and keying method at the same time [ref 3 chapter V page 6] Total JN-25 messages read by Washington per month during the first 9 months of 1942 estimated to be 2,500 on average. [ref 1, page 8] In August 1942 the D-10 version carried the bulk of the traffic, about equal to the amount of C-9 traffic before that version had been retired. In the third quarter of 1942 GY-1 is 207 personnel, 17 officers, 125 enlisted men, 15 civilian man and 50 civilian woman. [ref 1, page 4] This is over double the number present in the previous quarter and nearly ten times the number present in the final three months of 1941. 24 August 1942 battle of the Eastern Solomons. 1 October 1942 introduction of the E code book using additive book 11, JN-25E11, HA 1 RA 1, this runs until 30 November. First appearance of the E code book. So we now have 2 versions of the code book in use plus 4 additive books by various IJN units. Note unlike the D additive books in use the 11 book had only 50,000 text additives. This version was meant as a general purpose system for larger shore bases and all fleet units except submarines. (For the information on which code book was for what purpose see [ref 3 chapter V page 3]) With the introduction of the E-11 version there was a gradual build up until it and its successors took over as the version most messages were sent in during early 1943. During October 1942 the IJN begins a program of deception and drill traffic, continuing irregularly through 1943 [ref 1, page 2]. This is the first use of such traffic the US has noted since the deception traffic sent just before the start of the war. 16 October 1942, introduction of JN-25D16A Ge, RO 2 RA 1, and JN-25D16B Ge, RO 3 RA 2, changing from the 16 Jo to 16 Ge additive books, in use until 13 December. The 16 Jo A and B additive books had been in use since 15 August. 20 October 1942 additive book 10 Jo, in use since 15 August with the D version code book is replaced by additive book version 10 Ge, JN-25D10 Ge, RO 1 RA 1, which stays in use until 17 December. 24 October 1942, EFU, until 14 April 1943. Probably a minor cipher book, presumably the E code with the FU additive book. There is no IJN identifier or channel number given. 26 October 1942 Battle of Santa Cruz. 1 November JN-25F10 Ge, KO 3 RO 1 RA 1 Ge, this is first appearance of the F code book and uses the 10 Ge additive book. Used until 31 May 1943 after which it is retired. The F code was meant for auxiliary vessels, minor shore stations and resident naval officers. (For the information on which code book was for what purpose see [ref 3 chapter V page 3]) So the IJN has the D, E and F code books in use along with four additive books in the following combinations, D10 Go, D16A Go, D16B Go, E11 and F10 Ge. The USN called the D-10 version and its successors channel 1, the E-11 version and its successors channel 2, the D-16A and B and their successors channel 3 and the sequence beginning with F-10 channel 4. To restate, as introduced the channels were used as follows, Channel 1 General purpose for all naval forces excluding picket boats, gun boats, hospital and rescue ships and labour battalions. Channel 2 General purpose system for larger shore bases and all fleet units except submarines. Channel 3 General purpose system for high command. Channel 4 for auxiliary vessels, minor shore stations and resident naval officers. [ref 3 chapter V page 3 to 5]. It appears the IJN managed to confuse itself at times with so many versions in use, with the allies benefiting from mistakes like using the D code books with additive book 11 and the E code books with additive book 10. [ref 3 chapter V page 5] 12 November 1942 start of the naval battle of Guadalcanal. 1 December 1942 introduction of additive book 12 for E code, JN-25E12, HA 1 RA 1, in use until 2 January 1943. Note again unlike the D and F codes in use only 50,000 text additives are used. This replaces additive book 11 that had been introduced on 1 October 1942. 14 December 1942 introduction of JN-25D17A, RO 2 RA 2 and JN-25D17B, RO 3 RA 2, additive book 17 for the D code books, in use until 14 February 1943. These replaced the 16 Go books where they were in use. The 16 Go books had started use on 16 October 1942. 17 December 1942 introduction of additive book 13 for the D version, JN-25D13, RO 1 RA 2, until 14 February 1943 This replaced the 10Ge additive book that had been in use since 20 October 1942. Total JN-25 messages read by Washington per month during the last 3 months of 1942 estimated to be 6,000. [ref 1, page 8] Total JN-25 messages sent to Washington in the last 6 months of 1942, on average per month 17,000 plus 20,000 duplicates. [ref 1, page 7] In the fourth quarter of 1942 GY-1 is 299 personnel, 32 officers, 15 Waves officers, 168 enlisted men, 29 civilian man and 55 civilian woman. [ref 1, page 4] 3 January 1943 introduction of additive book 14 for the E version, JN-25E14, RA 1 RA 2, in use until 14 February 1943. Number of text additives raised to 100,000, same as the additive books currently in use with the D and F code books, from now until the J-36 version in December 1943 this will be the standard text additive size. Additive book 14 replaces book 12 which had been in use since 1 December 1942. 12 January 1943 EN code, in use until 14 April 1943, probably another minor version, presumably the E code book with the N additive book. There is no IJN identifier or channel number given. 20 January 1943 dummy "SUB CODE" until the end of the month. This is the first appearance of a dummy code. 15 February 1943 introduction of additive books 17A and 17B, JN-25E17A RO 2 RA 2 and also JN-25E17B, RO 3 RA 2, both in use until 25 February, this appears to be the replacing of the D code book with the E code book, while retaining the number 17A and B additives book that had been introduced on 14 December 1942. 15 February 1943 introduction additive book 14 for the D code book, JN-25D14, HA 1 RA 2, in use until 31 March. Also on this date introduction of the DQ version, JN-25DQ, RO 1 RA 3, in use until 31 March. Despite the obvious sequence of code and additive books it appears that D-14 is a supplement to channel 2, which is using the E code book, and is changing from E-14 to E-15 on this date. This means D-14 is not the replacement for the D-13 version being used in channel 1, instead the DQ version replaces the D-13 version that had been in use for channel 1 since 17 December 1942. This is the correct sequence when following the IJN identifiers. 15 February 1943 introduction of additive book 15 for the E code book JN-25E15, HA 1 RA 3, in use until 14 April, this replaces additive book 14 in use since 3 January 1943. In the E15 version of JN-25 a message begins with the relevant to/from information, a six digit plain text date/time group, a code group indicating what version of JN-25 is being used and the indicator group repeated twice. The final three groups of the message are an ending indicator, the last 5 digits of the date time group and finally a repeat of the version indicator group. February 1943, US recovers significant code materials from the I-1 sunk off Guadalcanal. Including a superceded JN-25 code book, but no additive book. "As part of the crew at Station AL Guadalcanal, I helped rehabilitate the five code books recovered plus many other classified documents and navigational charts. They were sent by courier to Pearl Harbor." [Phil Jacobsen, private communication.] 1 March 1943 introduction of the 20A (44) and 20B (44) additive books, JN-25E20A (44), RO 2 RA 3 and JN-25E20B (44), RO 3 RA 3. In use until 30 April. These additive books replaced the 17A and 17B books that had been in use since 15 February 1943. Total JN-25 messages read by Washington per month during the first 3 months of 1943 estimated to be 8,000. Of which 4,800 were current. Total messages sent to Washington per month 19,000 plus 50,000 duplicates. [ref 1, page 7-8] In the first quarter of 1943 GY-1 is 387 personnel, 46 officers, 23 Waves officers, 196 enlisted men, 60 enlisted waves, 26 civilian man and 36 civilian woman. [ref 1, page 4] 13 March 1943 Introduction of a dummy code, used until sometime in April. 1 April 1943 introduction of additive book 18a for D code book, JN-25D18a, RO 1 RA 4, in use until 14 April, replacing the Q additive book introduced on 15 February 1943 (JN-25DQ). With D-18 the number of key additives is raised from 1,000 to 2,000, this becomes standard until the J-36 version is introduced in December 1943. 5 April 1943, or around this date introduction of another dummy code which stays in service until 13 April. 15 April 1943 introduction of additive book 18b for D code book, JN-25D18b, RO 1 RA 4 , replacing the D-18a additive book, D-18b ends 31 May and this appears to be the final use of the D code book, at least before 4 August 1943. Also on this date the introduction of additive book 19 for E code book, JN-25E19, HA 1 RA 4, replacing the number 15 additive book introduced on 15 February 1943. E-19 ends on 14 June 1943. 15 April 1943 change made to the EN version, in use until 16 July after which it appears to end. Also on this date the USN has a record for the version called EFU, in use until 1 May when usage appears to end. EFU was introduced on 24 October 1942 and it is unclear why it is listed again on this date. Similar note for the EN version, introduced on 12 January 1943 and mentioned again on this date. 18 April 1943 the aircraft carrying Admiral Yamamoto is intercepted and shot down, killing the Admiral. 1 May 1943 introduction of additive books 23-A and 23-B for the E code books, JN-25E23A, RO 2 RA 4 and JN-25E23B, RO 3 RA 4 in use until 30 June. These books replace the 20-A (44) and 20-B (44) books introduced on 1 March 1943. 1 June 1943 JN-25H21, additive book 21 for H code book, RO 1 RA 5, in use until 7 July. This replaces the JN-25D18b system introduced on 15 April 1943. Also on this date introduction of JN-25K25, RU 1 RA 1, additive book 25 for the K code book, in use until 4 August 1943. This replaces the F-10 Ge version introduced on 1 November 1942. So the first appearance of the H and K code books. 15 June 1943 introduction of additive book 22 for E code book, JN-25E22, HA 1 RA 5, in use until 4 August 1943, replacing additive book 19 introduced on 15 April 1943. Total JN-25 messages read by Washington per month during the second 3 months of 1943 11,000. Of which 5,100 were current. Total messages sent to Washington per month 22,000 plus 70,000 duplicates. [ref 1, page 7-8] In the second quarter of 1943 GY-1 is 472 personnel, 47 officers, 29 Waves officers, 160 enlisted men, 185 enlisted waves, 20 civilian man and 31 civilian woman. [ref 1, page 4] 1 July 1943 introduction of additive book 29 for the E code books, JN-25E29A, RO 2 RA 5 and JN-25E29B, RO 3 RA 5 in use until 4 August 1943. These replaced the 23A and 23B additive books introduced on 1 May 1943. 7 July 1943 introduction of additive book 24 for H version JN-25H24, RO 1 RA 6 in use until 4 August, replacing additive book 21 introduced on 1 June 1943. Total JN-25 messages read by Washington during July 1943 16,800. Of which 15,700 were current. [ref 1, page 8] Total JN-25 messages read by Washington during August 1943 13,000. Of which 2,100 were current. [ref 1, page 8] Big JN-25 reorganisation on 5 August 1943, no less than 5 changes, J code books introduced, E code books retired. Things continue to become more complex, including old code and additive books being brought back into service. The above basic JN-25 version information comes from 4 pages of spreadsheets from reference 5 covering over 4 years from June 1939 to August 1943. The JN-25 information for August 1943 to the end of 1944 is another 5 spreadsheet pages. It includes further changes to the key additives system and even the return of previously retired versions for supplemental or other uses. The final entry is for JN-25 version N-77 (RO 2 RA 18) on 1 January 1945, which is the last issue of a JN-25 additive book [ref 3 chapter V page 9] To return to JN-25 versions in use between 1940 and 1942. As of 20 April 1945 the USN found it had 35,761 additives of JN-25B7, the version in use 1 August to 3 December 1941, with the probability several hundred might be bad. The recent decision to rework the B7 traffic, which was available in far greater amount than traffic in any other version, meant it was considered possible to recover most of the missing additives. JN-25B8, in use 4 December 1941 to 27 May 1942 had 47,340 text additives recovered but they included a large number of bad values, a quick check resulting in around 1,000 changes. In addition many of the B8 work book pages had been destroyed, requiring them to be rewritten, but it was hoped almost all additives could be recovered. [ref 5 workable traffic list dated 20 April 1945]. As of 21 August 1945 the recoveries by version were [ref 5 JN-25 key and additive recovery table], JN-25A5 999 out of 999 key additives, 4,907 out of 50,000 text additives. JN-25B6 999 out of 999 key additives, 45,321 out of 50,000 text additives. JN-25B7 999 out of 999 key additives, 47,590 out of 50,000 text additives. JN-25B8 999 out of 999 key additives, 48,835 out of 50,000 text additives. The following table is a restatement of the number of JN-25 messages read in Washington per month, table is time period, total read per month, total read that were in the current cipher, 1941 none and none January to September 1942 2,500 (estimated) and unknown October to December 1942 6,000 (estimated) and unknown January to March 1943 8,000 (estimated) and 4,800 (estimated) April to June 1943 11,000 and 5,100 July 1943 16,800 and 15,700 August 1943 13,000 and 2,100 September 1943 14,300 and 12,900 October 1943 17,800 and 9,300 November 1943 20,900 and 17,200 December 1943 16,600 and 1,700 JN-25 Messages received per month in Washington, table is time period, number of original messages, number of duplicates, 1941 7,000 and 11,000 January to June 1942 7,000 and 11,000 July to December 1942 17,000 and 20,000 January to March 1943 19,000 and 50,000 April to June 1943 22,000 and 70,000 July to September 1943 26,000 and 84,000 October to December 1943 30,000 and 96,000 Some 60 to 75% of the IJN messages received in Washington were in JN-25, in the period 1941 to 1943. Size of GY-1,USN code breaking unit in Washington In the first quarter of 1941 GY-1 is 10 personnel, 7 officers and 3 enlisted men. In the second quarter of 1941 GY-1 is 16 personnel, 9 officers, 5 enlisted men and 2 civilian men. In the third quarter of 1941 GY-1 is 20 personnel, 8 officers, 10 enlisted men and 2 civilian men. In the final quarter of 1941 GY-1 is 22 personnel, 9 officers, 10 enlisted men and 3 civilian men. In the first quarter of 1942 GY-1 is 41 personnel, 9 officers, 30 enlisted men, 1 civilian man and 1 civilian woman. In the second quarter of 1942 GY-1 is 98 personnel, 12 officers, 70 Enlisted men, 1 civilian man and 15 civilian woman. In the third quarter of 1942 GY-1 is 207 personnel, 17 officers, 125 Enlisted men, 15 civilian man and 50 civilian woman. In the fourth quarter of 1942 GY-1 is 299 personnel, 32 officers, 15 Waves officers, 168 enlisted men, 29 civilian man and 55 civilian woman. In the first quarter of 1943 GY-1 is 387 personnel, 46 officers, 23 Waves officers, 196 enlisted men, 60 enlisted waves, 26 civilian man and 36 civilian woman. In the second quarter of 1943 GY-1 is 472 personnel, 47 officers, 29 Waves officers, 160 enlisted men, 185 enlisted waves, 20 civilian man and 31 civilian woman. In the third quarter of 1943 GY-1 is 606 personnel, 60 officers, 47 Waves officers, 117 enlisted men, 336 enlisted waves, 12 civilian man and 34 civilian woman. In the fourth quarter of 1943 GY-1 is 656 personnel, 70 officers, 72 Waves officers, 108 enlisted men, 367 enlisted waves, 5 civilian man and 34 civilian woman. Allied code group meaning recovery status for JN-25A 1 December 1940 "approximately 1,300 values recovered" 1 January 1941 "approximately 1,400 values recovered" 1 March 1941 "approximately 1,600 values recovered" 1 April 1941 "approximately 1,800 values recovered" Allied code group meaning recovery status, for JN-25B, to 10 March 1942, March 1 1941: nil April 1, 1941: "approximately 300 values recovered" May 1, 1941: "approximately 400 values recovered" June 1, 1941: "approximately 1100 values recovered" July 1, 1941: "approximately 1100 values recovered" August 1, 1941: "approximately 2000 values recovered" Sept 1, 1941: "approximately 2000 values recovered" Oct 1, 1941: "approximately 2400 values recovered" "Completed during October 1941" Nov 1, 1941: "600 values recovered" [i.e., a total of 3,000 values as of this date] "Completed during November 1941" Dec 1, 1941: "800 values recovered" (i.e., a total of 3,800 values as of this date) Jan 1, 1942: "Approximately 6,180 values recovered". March 10, 1942, Corregidor notes 3522 confirmed, 70 good, 2185 questionable, 3531 very questionable and 939 no classification code group recoveries, total 10, 247 groups. JN-25 version usage JN-25A1, D IPPAN RA 1, start 1 June 1939, end 31 August 1939 JN-25A2, D IPPAN RA 2, start 1 September 1939, end 30 November 1939 JN-25A3, D IPPAN RA 3, start 1 December 1939, end 31 May 1940 JN-25A4, D IPPAN RA 4, start 1 June 1940, end 30 September 1940 JN-25A5, D IPPAN RA 5, start 1 October 1940, end 30 November 1940 JN-25B5, D IPPAN RA 5, start 1 December 1940, end 31 January 1941 JN-25B6, D IPPAN RA 6, start 1 February 1941, end 31 July 1941 JN-25B7, D IPPAN RA 7, start 1 August 1941, end 3 December 1941 JN-25B8, D IPPAN RA 8, start 4 December 1941, end 27 May 1942 JN-25C9, D IPPAN RA 9, start 28 May 1942, end 14 August 1942 JN-25D10 Jo, RO 1 RA 1, start 15 August 1942, end 19 October 1942 JN-25D16A Jo, RO 2 RA 1, start 15 August 1942, end 15 October 1942 JN-25D16B Jo, RO 3 RA 2, start 15 August 1942, end 15 October 1942 JN-25E11, HA 1 RA 1, start 1 October 1942, end 30 November 1942 JN-25D16A Ge, RO 2 RA 1, start 16 October 1942, end 13 December 1942 JN-25D16B Ge, RO 3 RA 2, start 16 October 1942, end 13 December 1942 JN-25D10 Ge, RO 1 RA 1, start 20 October 1942, end 17 December 1942 JN-25EFU, start 24 October 1942, end 14 April 1943 JN-25F10 Ge, KO 3 RO 1 RA 1 Ge, start 1 November 1942, end 31 May 1943 JN-25E12, HA 1 RA 1, start 1 December 1942, end 2 January 1943 JN-25D17A, RO 2 RA 2, start 14 December 1942, end 14 February 1943 JN-25D17B, RO 3 RA 2, start 14 December 1942, end 14 February 1943 JN-25D13, RO 1 RA 2, start 17 December 1942, end 14 February 1943 JN-25E14, HA 1 RA 2, start 3 January 1943, end 14 February 1943 JN-25EN, start 12 January 1943, end 14 April 1943 JN-25E17A, RO 2 RA 2, start 15 February 1943, end 28 February 1943 JN-25E17B, RO 3 RA 2, start 15 February 1943, end 28 February 1943 JN-25D14, HA 1 RA 2, start 15 February 1943, end 31 March 1943 JN-25E15, HA 1 RA 3, start 15 February 1943, end 14 April 1943 JN-25DQ, RO 1 RA 3, start 15 February 1943, end 31 March 1943 JN-25E20A, RO 2 RA 3, start 1 March 1943, end 30 April 1943 JN-25E20B, RO 3 RA 3, start 1 March 1943, end 30 April 1943 JN-25D18A, RO 1 RA 4, start 1 April 1943, end 14 April 1943 JN-25D18B, RO 1 RA 4, start 15 April 1943, end 31 May 1943 JN-25E19, HA 1 RA 4, start 15 April 1943, end 14 June 1943 JN-25EN, start 15 April 1943, end 16 July 1943 JN-25EFU, start 15 April 1943, end 1 May 1943 JN-25E23A, RO 2 RA 4, start 1 May 1943, end 30 June 1943 JN-25E23B, RO 3 RA 4, start 1 May 1943, end 30 June 1943 JN-25H21, RO 1 RA 5, start 1 June 1943, end 7 July 1943 JN-25K25, RU 1 RA 1, start 1 June 1943, end 4 August 1943 JN-25E22, HA 1 RA 5, start 15 June 1943, end 4 August 1943 JN-25E29A, RO 2 RA 5, start 1 July 1943, end 4 August 1943 JN-25E29B, RO 3 RA 5, start 1 July 1943, end 4 August 1943 JN-25H24, RO 1 RA 6, start 7 July 1943, end 4 August 1943. (The above is 4 pages of the listing, there is another 5 pages covering to 1 January 1945) Versions by channel, from the introduction of the channel system on 15 August 1942 until 4 August 1943 Channel 1, JN-25D10 Jo, RO 1 RA 1, start 15 August 1942, end 19 October 1942 JN-25D10 Ge, RO 1 RA 1, start 20 October 1942, end 17 December 1942 JN-25D13, RO 1 RA 2, start 17 December 1942, end 14 February 1943 JN-25DQ, RO 1 RA 3, start 15 February 1943, end 31 March 1943, (yes DQ) JN-25D18A, RO 1 RA 4, start 1 April 1943, end 14 April 1943 JN-25D18B, RO 1 RA 4, start 15 April 1943, end 31 May 1943 JN-25H21, RO 1 RA 5, start 1 June 1943, end 7 July 1943 JN-25H24, RO 1 RA 6, start 7 July 1943, end 4 August 1943. Channel 2, JN-25E11, HA 1 RA 1, start 1 October 1942, end 30 November 1942 JN-25E12, HA 1 RA 1, start 1 December 1942, end 2 January 1943 JN-25E14, HA 1 RA 2, start 3 January 1943, end 14 February 1943 JN-25D14, HA 1 RA 2, start 15 February 1943, end 31 March 1943 (yes D14) JN-25E15, HA 1 RA 3, start 15 February 1943, end 14 April 1943 JN-25E19, HA 1 RA 4, start 15 April 1943, end 14 June 1943 JN-25E22, HA 1 RA 5, start 15 June 1943, end 4 August 1943 Channel 3, JN-25D16A Jo, RO 2 RA 1, start 15 August 1942, end 15 October 1942 JN-25D16B Jo, RO 3 RA 2, start 15 August 1942, end 15 October 1942 JN-25D16A Ge, RO 2 RA 1, start 16 October 1942, end 13 December 1942 JN-25D16B Ge, RO 3 RA 2, start 16 October 1942, end 13 December 1942 JN-25D17A, RO 2 RA 2, start 14 December 1942, end 14 February 1943 JN-25D17B, RO 3 RA 2, start 14 December 1942, end 14 February 1943 JN-25E17A, RO 2 RA 2, start 15 February 1943, end 28 February 1943 JN-25E17B, RO 3 RA 2, start 15 February 1943, end 28 February 1943 JN-25E20A, RO 2 RA 3, start 1 March 1943, end 30 April 1943 JN-25E20B, RO 3 RA 3, start 1 March 1943, end 30 April 1943 JN-25E23A, RO 2 RA 4, start 1 May 1943, end 30 June 1943 JN-25E23B, RO 3 RA 4, start 1 May 1943, end 30 June 1943 JN-25E29A, RO 2 RA 5, start 1 July 1943, end 4 August 1943 JN-25E29B, RO 3 RA 5, start 1 July 1943, end 4 August 1943 Channel 4, JN-25F10 Ge, KO 3 RO 1 RA 1 Ge, start 1 November 1942, end 31 May 1943 JN-25K25, RU 1 RA 1, start 1 June 1943, end 4 August 1943 No channel number assigned by the allies, JN-25EFU, start 24 October 1942, end 14 April 1943 JN-25EN, start 12 January 1943, end 14 April 1943 JN-25EN, start 15 April 1943, end 16 July 1943 JN-25EFU, start 15 April 1943, end 1 May 1943 JN-25 key and text additives recovered by version, as of 21 August 1945. [ref 5 JN-25 Key and text additive recovery table]. Table is version; key additives total/ recovered; text additives total/recovered Version Key Text A-5 999/999 50,000/4,907 B-6 999/999 50,000/45,321 B-7 999/999 50,000/47,590 B-8 999/999 50,000/48,835 C-9 999/999 50,000/50,000 D-10 1,000/998 100,000/77,932 E-11 1,000/975 50,000/32,282 E-12 1,000/970 50,000/18,900 D-13 1,000/964 100,000/34,700 E-14 1,000/1,000 100,000/40,600 E-15 1,000/1,000 100,000/68,500 D-18 2,000/1,500 100,000/5,800 E-19 2,000/2,000 100,000/59,400 H-21 2,000/1,642 100,000/7,200 E-22 2,000/2,000 100,000/66,900 H-24 2,000/1,872 100,000/4,500 Final notes, other pre war IJN codes in use pre war and mentioned in the above references, •JN-4 a contact operational code, introduced on 1 December 1941 •JN-11, similar to JN-25. •JN-20 a "minor general purpose system" introduced 4 June 1940. •JN-36 and JN-37 weather systems, superceding plain text, introduced on 7 December 1941. •JN-40 another merchant ship code. •JN-50 The Merchant-Navy vessel liaison code, called JN-50, introduced in 1939. The US stole a code book and so could read the traffic from "fall 1939" until the revision on 10 August 1941. •JN-76 The administrative code, introduced on 1 November 1938, called AD then JN-76 •JN-79 The material code introduced in 1935 and called MAT then JN-79 •JN-82 The intelligence code, introduced in 1935 and called I then JN-82 All up the IJN used some 184 code systems during the war, these code systems used 1,007 individual ciphers. [ref 3 chapter V page 2] Other code information from other references, these may have been introduced pre war or during the war, and yes some of this information is very tentative, •JN-4 straight list of code groups to transmit, 4 kana. •JN-11 four figure code groups, similar to JN-25, fleet auxiliary system. •Also the related system JN-147 and possibly JN-14. •JN-12? Minefields •JN-39 merchant ship cipher introduced in May 1940 and changed in February 1941 after theft of the books was suspected. •JN-40 merchant shipping cipher, first broken in September or November 1942) Called the MARU code by the allies at times. •JN-152 navigation warnings •JN-153 naval air code. •JN-166 naval air/weather code •JN-167 merchant ship code.
Works Cited
Boyd, Carol. Hitler's Japanese Confidant. Kansas: University Press of
Kansas, 1993.
Kahn, David. The Codebreakers. The Story of Secret Writing. New York:
Macmillan Company, 1967.
Kahn, David. Kahn on Codes. Secrets of the New Cryptology. New York:
Macmillan Publishing, 1983.